Kioptrix Level 1
So let me start with the setup.
I have my HP Pavilion Notebook as my base system. I have installed VMware Workstation 15 Player and installed Kali linux into it as per the following setup:
Memory: 4 GB
Hard Disk: 80 GB
Network Adapter: NAT
And for the target machine, I have installed Kioptrix Level 1 from Vulnhub with the following setup:
Memory: 256 MB
Hard Disk: 3 GB
Network Adapter: NAT
Lets start some reconnaissance now.
First, lets check the ip of our Kali machine and start with some scanning to find our target machine.
 So the IP of our Kali machine is: 192.168.227.130.
So the IP of our Kali machine is: 192.168.227.130.
Lets scan for the target machine now.
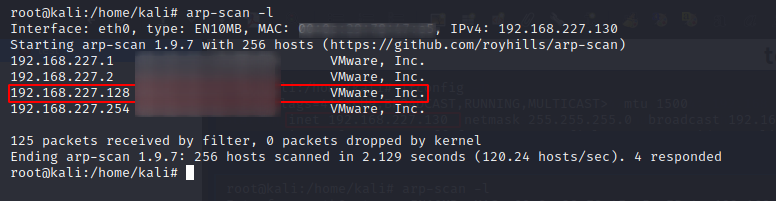 We have found our target machin's IP as: 192.168.227.128.Lets dig deeper and run Nmap to find out more about our target machine. As a practice, I create a folder structure for each individual machine that I recon to segregate for my reporting. Generally, I keep all the scan results from NMap, Nikto, Metasploit etc. into a folder called ScanResults; screenshots into a separate folder called imageproofs and so on.
We have found our target machin's IP as: 192.168.227.128.Lets dig deeper and run Nmap to find out more about our target machine. As a practice, I create a folder structure for each individual machine that I recon to segregate for my reporting. Generally, I keep all the scan results from NMap, Nikto, Metasploit etc. into a folder called ScanResults; screenshots into a separate folder called imageproofs and so on.
So lets run Nmap now
 The focus points from the nmap result has already been highlighted in the above image. Tcp ports 80 and 443 are open and it must be a Webserver. Lets try opening the webpage and see if we can find anything special there.
The focus points from the nmap result has already been highlighted in the above image. Tcp ports 80 and 443 are open and it must be a Webserver. Lets try opening the webpage and see if we can find anything special there.
 This is a default webpage and looks like we have 2 links here. Clicking on the links does not show any page but these links give the Apache version at the least.
This is a default webpage and looks like we have 2 links here. Clicking on the links does not show any page but these links give the Apache version at the least.

 All right, since the Tcp ports 80 and 443 are open, lets do a check using Nikto to see what details might come up.
All right, since the Tcp ports 80 and 443 are open, lets do a check using Nikto to see what details might come up.
 So far, we have the below findings from all of our recons above:
So far, we have the below findings from all of our recons above:
1. Open ports - 80 and 443 and these disclose some additional information in terms of the Apache version.
2. mod_ssl/2.8.4 OpenSSL/0.9.6b in use
3. SMB port 139 is open.
Lets try to find some more in regards to the SMB service using Metasploit.

 Lets add this to our notes as well - Samba 2.2.1a and see if we can access any of the shares using sambaclient.
Lets add this to our notes as well - Samba 2.2.1a and see if we can access any of the shares using sambaclient.
 So there are 2 shares here: ADMIN$ and IPC$. Try connecting to each just to see if we can find anything there.
So there are 2 shares here: ADMIN$ and IPC$. Try connecting to each just to see if we can find anything there.

 So we could not get to the ADMIN share but we could get to the default IPC share.
So we could not get to the ADMIN share but we could get to the default IPC share.
Moving along, before going and exploting the vulnerability, lets try to do the last recon activity of traversing various folder using dirbuster and see if we find bit more from any of the directories.


 We did see some more information publicly available in the folders, which is not ideal.
We did see some more information publicly available in the folders, which is not ideal.
So lets begins with the Samba 2.2.1a. There appears to be a CVE already and we have steps for for this as well (trans2open) in the rapid7 site which we can use to gain access of Kioptrix machine. So lets fireup Metasploit and get to it.

 Seems we are unsuccessful with this payload. Lets try changing to a non-staging payload and retry.
Seems we are unsuccessful with this payload. Lets try changing to a non-staging payload and retry.


Awesome ! so we have got the root access.
All right, lets check on the second vulnerability related to ssl and see if we can get through that as well
After searching for mod_ssl/2.8.4 OpenSSL/0.9.6b, we have come across the OpenLuck in github. So lets use that:
After following the procedures and compiling the c code using gcc, lets run it.

 We can see the list of parameters to be provided including the supported offsets. And based on our target machine, we have found 2 matching records, lets try with 0x6a first:
We can see the list of parameters to be provided including the supported offsets. And based on our target machine, we have found 2 matching records, lets try with 0x6a first:
 We could not get through with the first option, lets try again with 0x6b now
We could not get through with the first option, lets try again with 0x6b now

Awesome !! we got the root access again.
I will come back with the writeup for Kioptrix Level 2 machine. Thanks for reading.